In today’s business environment, companies are increasingly relying on third-party vendors to provide specialized services and products. While this strategy can offer significant benefits, it also comes with risks that must be managed effectively. One of the most critical risks is the potential exposure of sensitive business data to unauthorized parties. To mitigate this risk, it is essential for companies to establish robust third-party data protection measures. In this post, we will discuss five best practices that can help businesses protect their data when working with third-party vendors.
Conducting Thorough Due Diligence

Source: amaxra.com
The first best practice for protecting business data when working with third-party vendors is to conduct thorough due diligence. This process involves researching and vetting potential vendors to ensure that they have the necessary skills, experience, and reputation to meet the company’s needs. During the vetting process, it is essential to ask the right questions to understand the vendor’s data protection practices and policies. For example, you could inquire about the types of data they will be handling, how they plan to protect that data, and whether they have experienced any data breaches in the past.
In addition to asking these questions, it is important to verify that the vendor is compliant with industry regulations. Depending on the industry, there may be specific laws and regulations that govern the handling of sensitive data. It is essential to ensure that the vendor understands and complies with these regulations to avoid any legal and financial liabilities.
Establishing Clear Contractual Obligations
It is essential to include data protection requirements in vendor contracts to ensure that vendors understand their responsibilities and obligations regarding the protection of your business data. This includes defining and outlining data security expectations and ensuring that the contract includes provisions for vendor accountability and penalties for noncompliance.
When drafting contracts with vendors, work with legal counsel to ensure that the contract language is precise, unambiguous, and enforceable. The contract should specify the types of data that will be shared, how that data will be used, and how it will be protected. Additionally, it is important to ensure that the contract includes provisions for the termination of the contract if the vendor fails to meet its data protection obligations.
Implementing Data Security Protocols

Source: icxmsp.com
According to mamori.io, this involves implementing cybersecurity protocols for third-party vendors and educating vendors on best practices for data security. It is also important to regularly test vendor systems for vulnerabilities to identify and address potential security issues.
Cybersecurity protocols can include measures such as password protection, access control, encryption, and regular system updates. It is essential to educate vendors on these protocols to ensure that they understand the importance of protecting business data and the consequences of failing to do so. Regularly testing vendor systems for vulnerabilities can help to identify security weaknesses and enable businesses to take corrective action before a data breach occurs.
Moreover, organizations should establish clear guidelines and policies regarding cybersecurity practices to ensure consistent implementation across all departments. Regular training sessions and workshops should be conducted to keep employees updated on the latest threats and best practices for maintaining a secure digital environment. This includes educating them on the importance of identifying phishing attempts, avoiding suspicious links or attachments, and being cautious when sharing sensitive information.
Additionally, organizations should consider implementing advanced security measures such as intrusion detection systems, firewalls, and security incident response teams to detect and respond to any potential breaches swiftly. By adopting a proactive approach to cybersecurity, businesses can minimize the risk of data breaches and protect their valuable assets and reputation.
Regularly Monitoring And Auditing Vendors
The fourth best practice for protecting business data when working with third-party vendors is to regularly monitor and audit vendors. This involves ongoing monitoring of vendors to ensure that they are complying with data protection requirements and regularly auditing vendor systems for compliance. Continuously assessing vendor risk and taking necessary actions can help businesses to identify potential data protection risks and address them before they become significant threats.
Monitoring vendors can involve reviewing their systems for data protection compliance, reviewing vendor reports, and conducting periodic site visits. Auditing vendor systems can involve reviewing access logs, system configurations, and data storage practices to ensure that they comply with data protection requirements. It is important to work with vendors to address any issues that are identified during monitoring and auditing activities.
Using Third-Party Risk Management Software
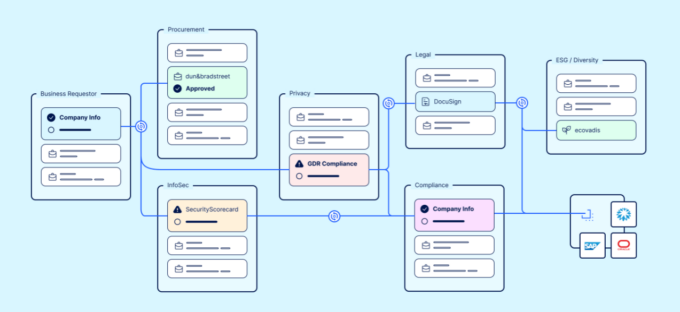
Certa TPRM software provides businesses with a comprehensive solution for managing vendor risk and ensuring data protection compliance. It allows companies to automate many of the vendor management processes and provides real-time visibility into vendor risk.
TPRM software can help businesses to streamline the due diligence process by providing a centralized platform for vendor research and vetting. It also allows businesses to establish and enforce data protection requirements through contractual obligations and provides ongoing monitoring and auditing capabilities. In addition, TPRM tools can enable businesses to identify and manage vendor risk across the entire vendor ecosystem, ensuring that data protection risks are identified and addressed before they become significant threats.
When it comes to selecting third-party risk management (TPRM) software, there are a few key factors to consider. First, it’s important to evaluate the software’s capabilities and ensure that it aligns with your business’s specific needs and risk management objectives. Look for a solution that can automate and streamline many of the vendor management processes, including due diligence, risk assessment, contract management, and ongoing monitoring.
Another important consideration is the software’s scalability and flexibility. Choose a solution that can grow and adapt with your business, as your vendor ecosystem and risk management needs evolve over time.
It’s also essential to evaluate the software’s data protection and security features, particularly if it will be handling sensitive or confidential information. Look for a solution that offers robust encryption, access controls, and monitoring capabilities to ensure that your data is protected at all times.
Protecting business data when working with third-party vendors is a critical concern for companies in today’s business environment. Implementing best practices such as conducting thorough due diligence, establishing clear contractual obligations, implementing data security protocols, regularly monitoring and auditing vendors, and using third-party risk management software can help businesses to mitigate the risk of data breaches and protect sensitive business information.
By implementing these practices, companies can ensure that they are managing vendor risk effectively and protecting their data from unauthorized access or exposure. As with any data protection strategy, it is essential to regularly review and update your approach to ensure that it remains effective and relevant in the face of evolving threats and regulations. By doing so, businesses can help to safeguard their data and ensure the trust and confidence of their customers and stakeholders.







