Yes, you have a booming online business. But do you ever stop to think about Internet security? As your company grows, so does your risk of a data breach or unfortunate security mishap. Hackers, viruses, and phishing scams all pose threats to your company’s success, and you can’t just ignore them. You need security that works: protection that doesn’t get in the way and protects you from everything.
Common IT security attacks
It does not matter how big or small your company is; you will always be a target for cyber-attackers. Your company will be targeted because you are perceived as an easy target. The widely publicized breaches in high-profile companies have led to the belief that only big companies get attacked by hackers.
In fact, smaller businesses and organizations with less secure IT systems, who have little or no security policy in place, are more likely to be attacked and suffer a security breach. Common IT attacks include:
Malware

Source: packetlabs.net
Malware is short for “malicious software.” Malware is a type of computer program that’s designed to cause trouble on your computer, such as by deleting your files or gathering information about you without your knowledge.
Malware can be installed on a computer via clicking on an infected link or downloading malicious software, such as a virus, worm, or Trojan horse. Malware is often hidden in free downloads, such as an online game.
Malware can be used by hackers to collect sensitive information from your device, such as credit card numbers, bank accounts, and passwords. The main danger of malware is that it can steal personal information and use it to commit other crimes in your name.
Phishing

Source: gridinsoft.com
Phishing is the most common way hackers gain access to people’s personal data. This type of attack occurs when a hacker sends an email or text message that looks like it came from a legitimate source. The phishing “email” will often urge you to click on a link in the email, take some action, and provide personal information like your Social Security number or bank account information. Phishing can occur through other channels as well, including fake websites and phone calls.
How is phishing dangerous to IT security?
To start with, if you fall for a phishing scam and enter in your username and password, now the attacker has access to your account. They can use it for their own purposes and may even change your password so that you no longer have access.
Once they have access, they can do things like download confidential company data and sell it on the black market or make fraudulent purchases using company funds. It could also lead to identity theft as they gain access to credit card numbers or social security numbers.
They could also send out more phishing emails from your email address, posing as a trusted source in an attempt to trick more people into giving up their credentials.
Man in the middle
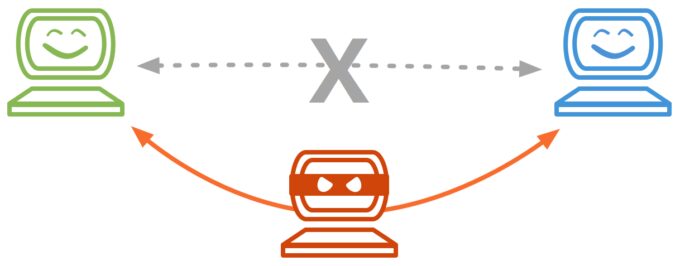
Source: medium.com
This is where a malicious actor inserts him/herself into a conversation between two parties, impersonates both parties and gains access to information that the two parties were trying to send to each other. This term can apply to any type of conversation or communication between two parties but is most commonly associated with cyberattacks.
In computer security, man-in-the-middle attacks can happen when you’re using an unsecured wireless network, such as the one you might find at a coffee shop or airport. A hacker could set up an access point there that’s indistinguishable from the real one, and any data you send over that connection is visible to them.
This can also happen on a computer network if an attacker has gained access to it or is able to set up a device on it that can intercept traffic. An attacker could also use malware installed on your computer to use it as a bridge for monitoring your network communications. In some cases, attackers can even get between you and a legitimate website by injecting themselves into your Internet service provider’s infrastructure (this is known as “ISP rerouting” or “rogue DNS”).
Denial of service attacks

Source: techrepublic.com
A denial of service (DoS) attack is when a hacker attempts to make a computer or network unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely.
Someone who commits a denial-of-service attack typically targets high-profile sites or services hosted on web servers, such as banks, credit card payment gateways, and even root name servers.
How dangerous is DOS?
- Denial of service attacks is dangerous because they can take down a website and make it inaccessible for a period of time.
- An attacker can use a denial of service attack to make it difficult for legitimate users to access the website or service that is being attacked.
- Denial of service attacks can be costly to organizations because they are forced to stop working until the attack has been mitigated.
- DoS attacks can be used by hackers as a smokescreen to hide other types of attacks that are happening at the same time.
Keylogging

Source: proofpoint.com
Keyloggers are software programs that run in the background of a computer and record every keystroke made. The information is sent to an attacker or stored locally, allowing the attacker access to login credentials and other sensitive information.
Keyloggers are used for a variety of uses, from tracking company employee activity to monitoring your children’s usage. Hackers use keylogging software to steal login credentials such as usernames and passwords, credit card details, and other personal information. Some keyloggers are even able to monitor social media accounts like Facebook, Skype, and Twitter.
What causes IT security issues?

Source: unsplash.com
Implementation and configuration errors
Implementation and configuration errors are the root cause of many IT security issues, particularly in the application security domain. These problems occur during coding, development, and deployment phases and can be difficult to detect. Configuration errors occur after a system is deployed when users change the default values of system settings.
Both types of errors can lead to vulnerability in your IT system and an increase in your attack surface area. Here are some examples of implementation and configuration errors:
- Missing or incomplete input validation checks
- Improper error handling that exposes sensitive information
- Insecure cryptographic storage
- Missing or incomplete authorization checks
Human error
Human error is another cause of IT security issues. There is no way to prevent it, and that makes it a threat to every organization. Mistakes can happen at any time, whether it’s an employee who clicks on a malicious link or someone in the IT department who accidentally opens a backdoor for hackers. In many cases, human error is simply unavoidable.
The reason why this type of vulnerability can be so dangerous is because people are unpredictable. They may not be able to control their actions, which means they could do something that leads to an attack without even realizing it. This makes it very difficult for companies to protect themselves against these threats.
Management failure
Management failure can cause IT security issues in several ways, including:
- Not having a written security policy. Every business should have a written security policy, whether it’s a one-page document or a multi-page manual. The lack of a written policy indicates that management is not serious about protecting the business’s IT assets. This is especially true if you’re subject to regulations or compliance requirements.
- Not enforcing the security policy. Even if you have a good security policy, it won’t help if management doesn’t enforce it and make sure employees are following its guidelines.
- Expecting IT staff to handle everything. While IT staff should be responsible for information technology and security, they shouldn’t be responsible for implementing and enforcing policies, educating employees, or ensuring compliance. These tasks belong squarely on management’s shoulders, and they should be held accountable for them.
- Outsourcing important functions without due diligence. It’s common for businesses to outsource functions like payroll and human resources (HR). It’s not unheard of for small businesses to even outsource their accounting to third parties. If you do so, make sure you check the company’s reputation carefully.
The key takeaway here is to get your security right. Not only do you not want to be in a position where you could be liable for data loss, but it’s just good practice to have a reliable backup of your files and information. In the digital age, data loss can be catastrophic and having an IT security partner like MyTek can help your company be secure and thrive.







